information security risk assessment template security risk Creating an information security risk assessment template for your organization isn t a quick or easy process You can t expect to show up to work at 9 a m and have your information security risk assessment template templates security risk A security risk assessment template is very important when you provide your private information to anyone or shift to a new place Download a security risk assessment template from here fill in the required details and print it out
Statistics Data and Systems CMS The Centers for Medicare Medicaid Services CMS Information Security Risk Assessment IS RA Procedure presents a systematic approach for the identification and mitigation of both business and system risks information security risk assessment template risk What Is the Purpose of a Security Risk Assessment Conducting a security risk assessment even one based on a free assessment template is a vital process for any business looking to safeguard valuable information RISK MANAGEMENT Scott Ritchie Manager HA W Information Assurance Services ISACA Atlanta Chapter Geek Week Security Framework Risk Assessment
examplesplianceforge cybersecurity risk assessment NIST SP 800 39 Managing Information Security Risk Risk Analysis Scope The scope of this risk assessment encompasses the potential risks and vulnerabilities to the confidentiality availability and integrity of all systems and data that ACME creates receives maintains or transmits information security risk assessment template RISK MANAGEMENT Scott Ritchie Manager HA W Information Assurance Services ISACA Atlanta Chapter Geek Week Security Framework Risk Assessment mass gov Security for State Employees Risk AssessmentInformation security risk assessment is an on going process of discovering correcting and preventing security problems The risk assessment is an integral part of a risk management process designed to provide appropriate levels of
information security risk assessment template Gallery
vendor rating template it risk assessment security countermeasures should new, image source: propulse.co

cyber security risk assessment example, image source: www.rakebackbible.com

Key components of risk management process, image source: www.researchgate.net
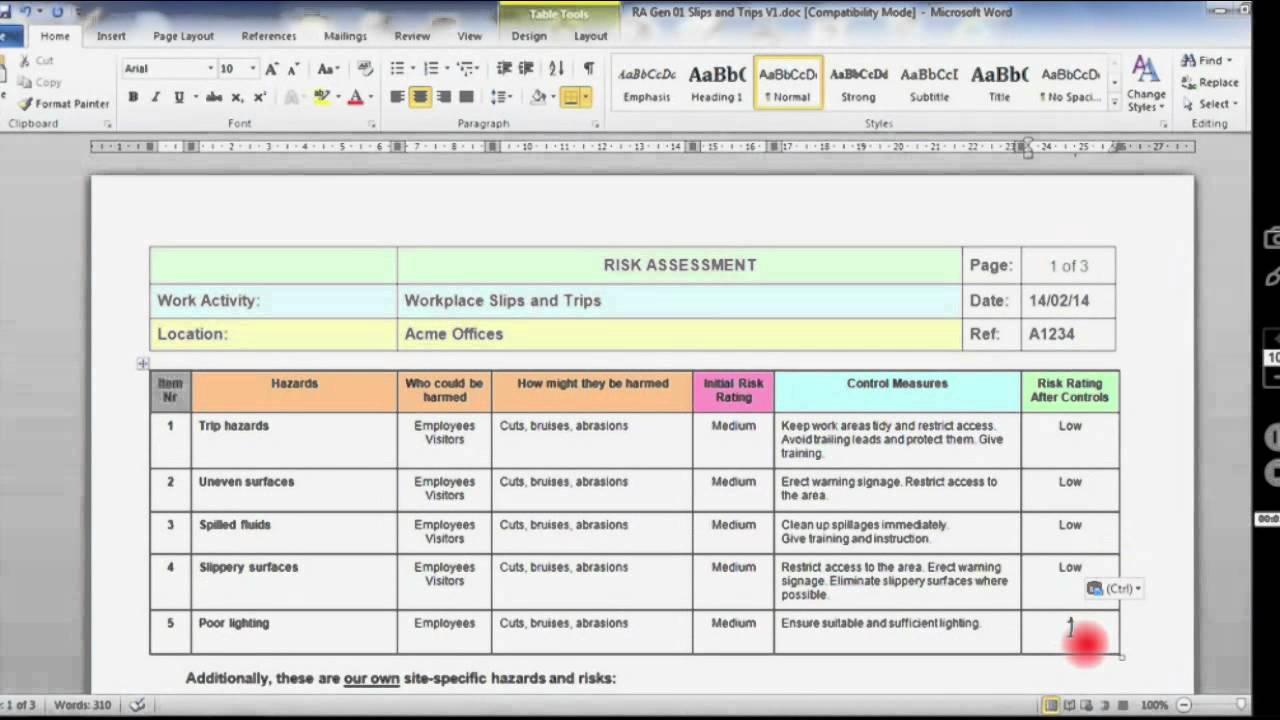
maxresdefault, image source: www.youtube.com
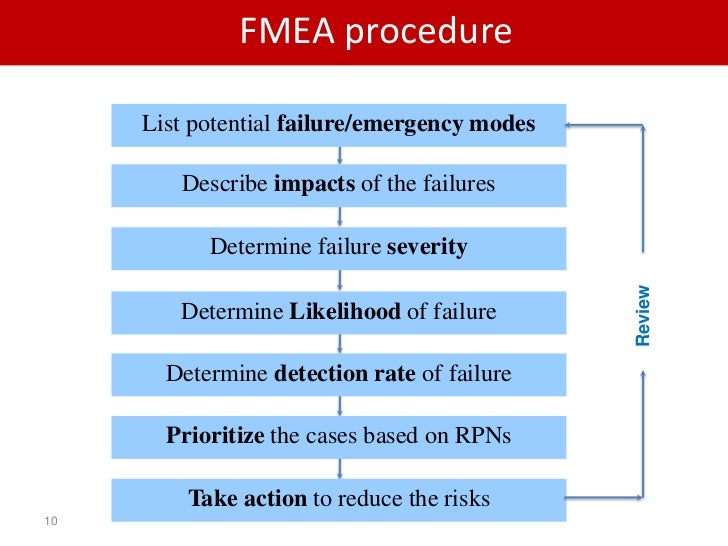
fmea most common risk assessment method in industry 6 728, image source: www.slideshare.net
Risk management framework, image source: en.wikipedia.org
Risk summary report, image source: www.vigilantsoftware.co.uk
enterprise security architecture from access to audit 11 728, image source: www.slideshare.net

fig5 7, image source: www.globalsecurity.org
25, image source: www.informationsecuritybuzz.com
meaningful use risk analysis how to conduct comprehensive security risk analysis 30 728, image source: www.slideshare.net
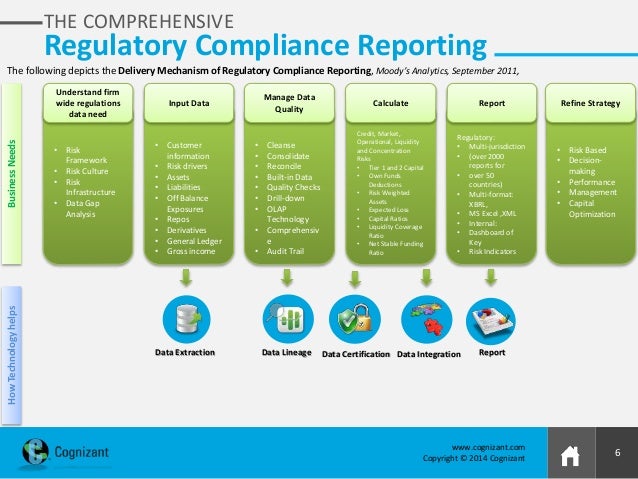
how cognizants zdlc solution is helping data lineage for compliance to basel iii 6 638, image source: www.pinsdaddy.com
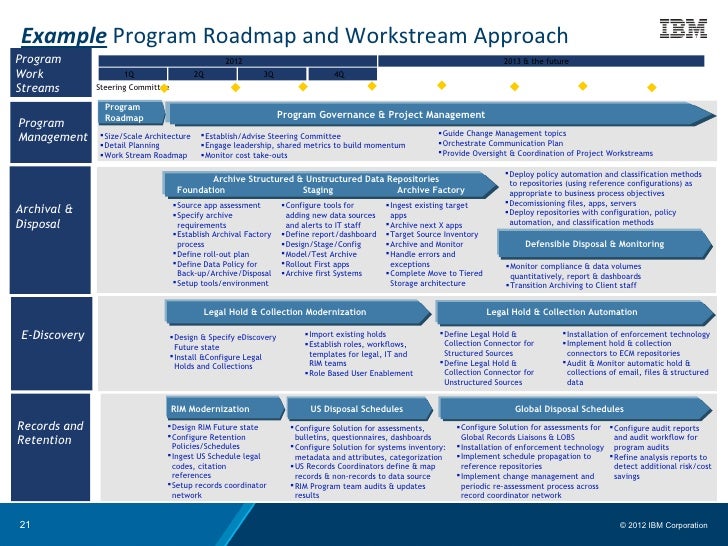
powerpoint tom 21 728, image source: www.slideshare.net
Audit ready Statement of Applicability 1, image source: www.vigilantsoftware.co.uk

restaurant pre opening checklist l2, image source: www.formsbirds.com

j1002 developing an infor4, image source: www.isaca.org
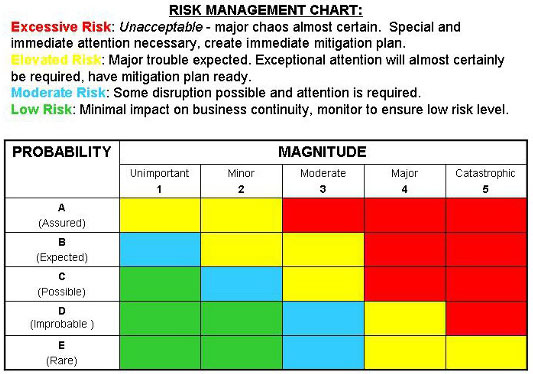
ditullio_fig1, image source: www.meddeviceonline.com
One_1, image source: www.tenable.com
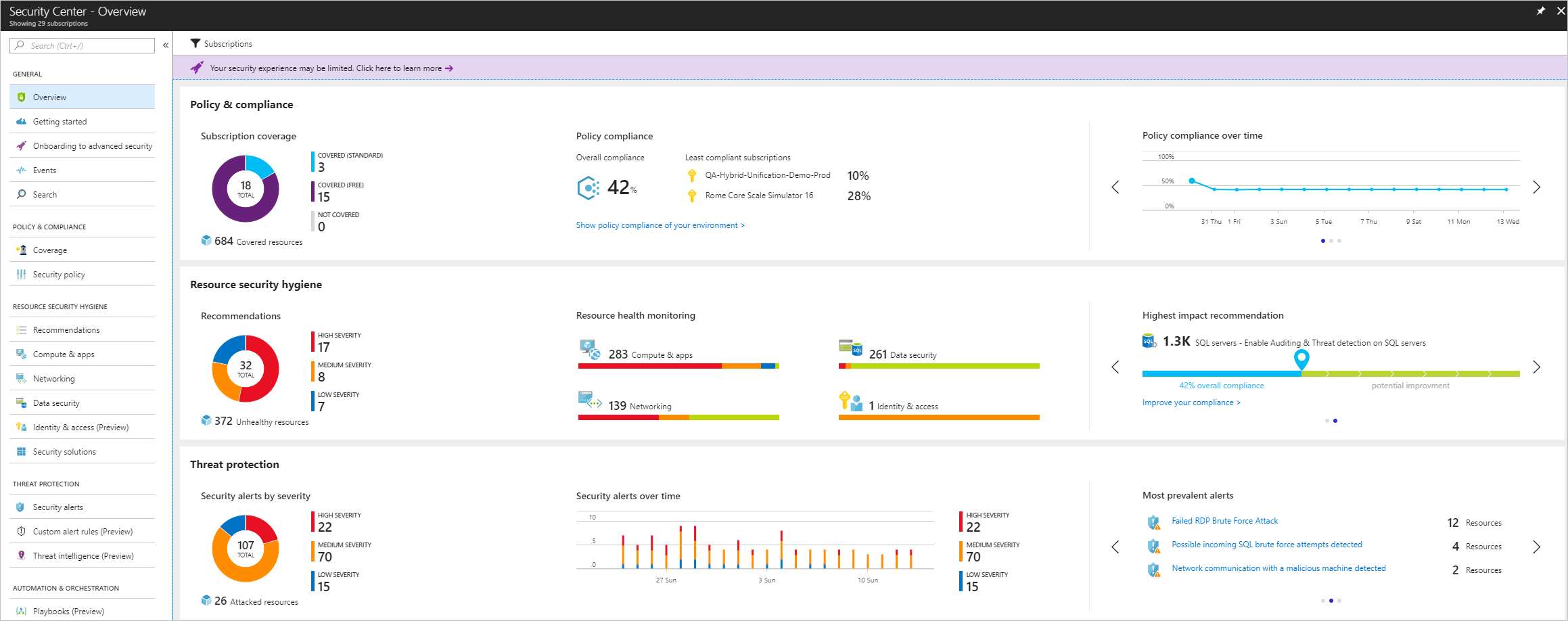
security center monitoring fig1 newui 2017, image source: docs.microsoft.com

swms_number, image source: www.safetyculture.com.au

